Invisibility on the networks. Lesson by Julian Oliver
Published 15 May 2018 by Laurent Catala
We attended the counter-surveillance boot-camp led by the hacktivist coder artist Julian Oliver at the Geneva Mapping Festival on May 10. An opportunity to explore and become aware of our permeability regarding networks.
Geneva, special envoy (text and photos)
Great success for the Mapping LAB workshop day, part of the 14th edition of the Geneva Mapping Festival (from May 9-12, 2018), full up on May 10. In the brand new setting of the Head (Haute école d’art et de design) campus in Geneva, the varied and motivated public brought together geeks, budding practitioners and neophytes, who came to familiarize themselves or improve their knowledge on plenty of subjects. Thirteen workshops were dedicated to machine learning, augmented reality, data visualization, interface prototyping, making synthesizers, or still “counter-surveillance”. We chose to attend the high-flying Network Counter-Surveillance Boot-Camp led by the artist and hacktivist engineer Julian Oliver.

The New Zealander resident in Berlin is known for his ironic sense of humor. The day before, he gave the audience a glimpse of it during a conference on the links between utopia and dystopia, mentioning his feeble hope for a future already bearing the hallmarks of climate change: “We are relishing the announced end of the world as if it were a show instead of taking the necessary decisions,” he says, hitting the audience with that statement while granting artists credit to carry a (slim) hope of establishing a new “global subjectivity.”
For his boot-camp, Oliver proposed an exploration of wireless networks (Wi-Fi but also telephone networks) to model the threats and surveillance tactics that spy on us daily, and be able to protect ourselves from them. But, in particular, provide a terrifying overview of the volatility of the data around us and the permeability of the personal information that passes through these networks.
Ghost machines
“The air of large cities is filled to the brim with data,” he says ironically as an introduction. Enough to make it unbreathable for good? A breath of fresh air is necessary prior to the workshop in order to confront ourselves with the abstraction of this IT free dive at the heart of the network.

First step, explains Oliver: protect the internal system of your computer before connecting yourself to the Wi-Fi network in hacker mode. You equip yourself with an Oracle VM, better known as a Virtual Box, free software that allows you to virtualize operating systems by creating false machines on your machine and thus making your computer inaccessible.
Second step: reinitiate your computer address (do not mistake it with the IP address, the router address that gets you connected to the network). Still a legal procedure, although some countries like the US would like to ban it. This is an effective way of breaking up the traceability of your connection. According to Oliver, neither the States nor the omnipotent access providers and other large internet companies want to protect your anonymity on the Web!

Third step: each participant activates his Virtual Box, then the network card via a USB key to which is linked a high-quality Wi-Fi detection antenna. When you open the dialogue box of the Virtual Box you can navigate through data using a whole series of code lines. From there on…Oliver moves forward alone, and we follow him with a mix of sci-fi fascination and paranoid anxiety. An IP address allows him to slip through information lists and other connection points that transit from all the terminals (computers, mobiles) located close by—the connection scale is approximately one hundred meters, he explains, but depends on environmental parameters (walls, network saturation, etc.)
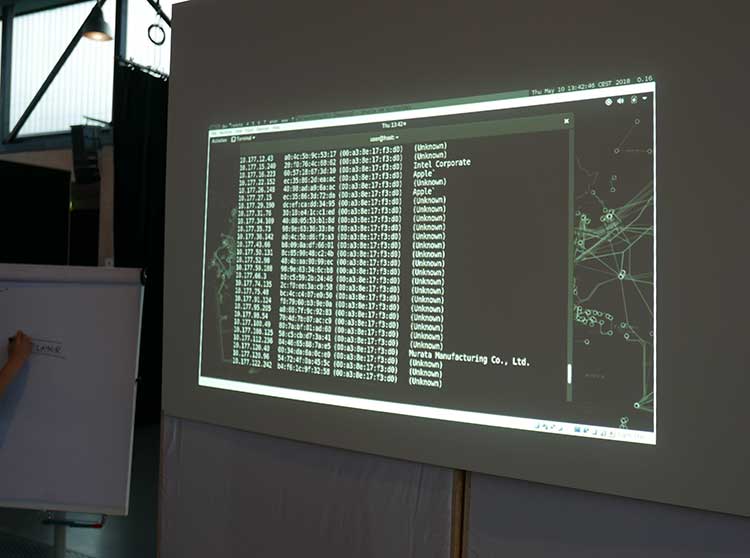
Oliver goes down into the heart of surrounding data with incredible ease, which makes us wonder about the general modus operandi—if these commands exist to penetrate at the heart of our data, everything is therefore planed at the root by manufacturers and other access providers for the trap to close in on the user. All the scanned data is recordable and particularly easily decipherable via software such as Wireshark, a free network analyzer of packets (name given to files passing through the network and containing traceability information, protocols and of course our precious data). There again, the demonstration is conclusive, and after a certain time (the network is temperamental), the information appears with its precise denomination, PNG or text files, and other URLs.
DIY relay antenna

Oliver barely had time to catch his breath before he moved on to the next step, the one concerning another type of wireless network, that of our mobile phones through the GSM network. By using a self-designed (and thus totally illegal) mobile phone relay antenna, Oliver scans the network on a 900 MHz frequency. Rapidly, he manages to connect his own DIY phone server via a program called YateBTS that appears on the list of available networks. In a few seconds, we were able to call each other and send SMS, totally free of charge. “One has to ask oneself why we pay as much when in fact the network is just there, accessible to all,” laughs out Oliver.

So, we are in fact under surveillance… and being robbed. How, then, does one protect oneself when one doesn’t have Mister Oliver’s hacking talent? “What you need to know is that when you go onto a website, it isn’t you who is connected, it’s the website that has just connected to you, via your request, he clarifies. All these accesses are under direct control from access providers that ignore nothing of your connections and the precious and moneymaking mass of information they contain.” Objective: protecting oneself in order to prevent the administrator, but also the visited website via SSL type security protocols, from knowing everything about you.
Since these protocols are often incomplete, encrypting data but leaving the visited URL address transparent, Oliver advises to opt for browsers using the tunnel principle (that makes the connection bounce via a multitude of volunteer intermediaries, located in different countries, and assigns you a totally fictive IP address, since located in another country), such as Tor, or going through a virtual private network (VPN). And even so, access to a website through the Tor browser can be easily detectable (and thus blocked) whereas VPNs aren’t all totally secure. Depending on the network to which you connect, your access provider and the possible proxies installed, downloading anonymous browsers or VPNs can be downright impossible. You can get the famous message “pirates are trying to steal your data” as it was the case at the Head; that takes the cake in the boot-camp context! Last advice from Julian Oliver: without resorting to download, search engines like duckduckgo still offer a little confidentiality.
More information on Julian Oliver and on the Mapping Festival 2018
